1. 来自Google的Project Zero团队的新闻和更新
https://googleprojectzero.blogspot.com/2018/08/the-problems-and-promise-of-webassembly.html
2. https://github.com/ohpe/juicy-potato#juicy-potato-abusing-the-golden-privileges
3. https://github.com/calebmadrigal/trackerjacker
4. https://github.com/JamesNewton/DroidScriptBusPirate
5. Foreshadow Attacks – 发现3个新的Intel CPU侧通道缺陷
https://thehackernews.com/2018/08/foreshadow-intel-processor-vulnerability.html
6. Microsoft.Workflow.Compiler.exe中的任意,未签名的代码执行向量
https://posts.specterops.io/arbitrary-unsigned-code-execution-vector-in-microsoft-workflow-compiler-exe-3d9294bc5efb
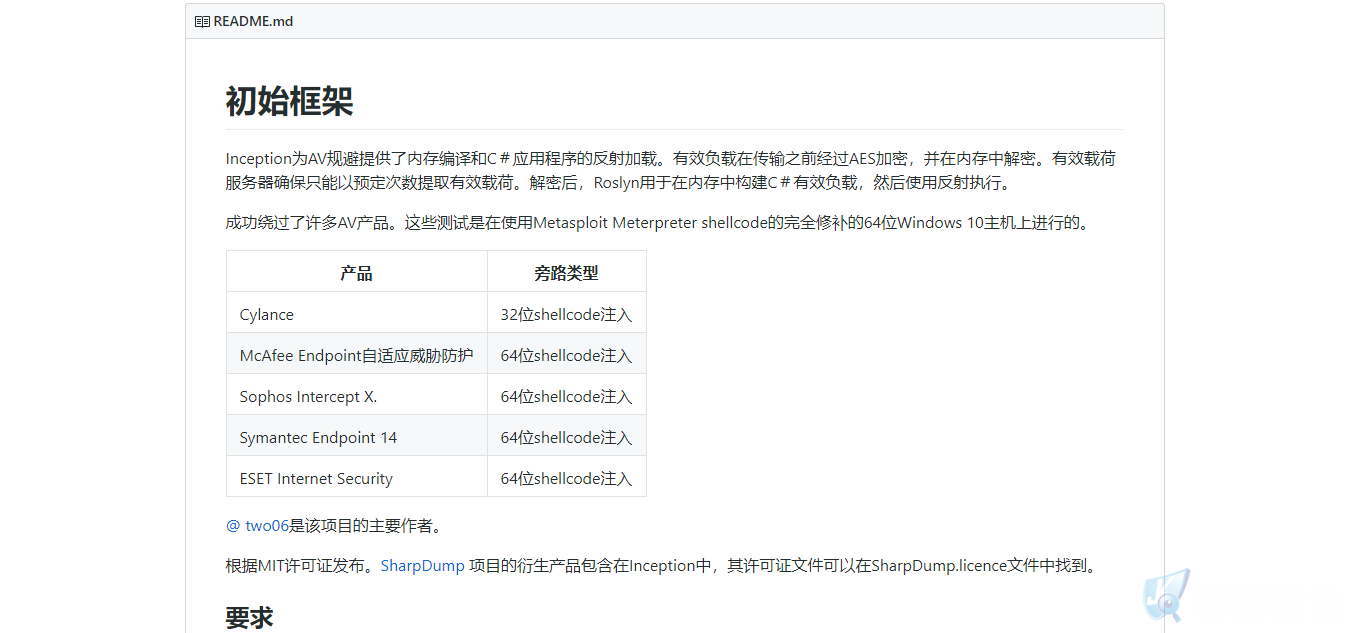
7. https://github.com/two06/Inception
8. 反射DLL和你
Reflective DLLs and You
9. https://github.com/infosecn1nja/Red-Teaming-Toolkit
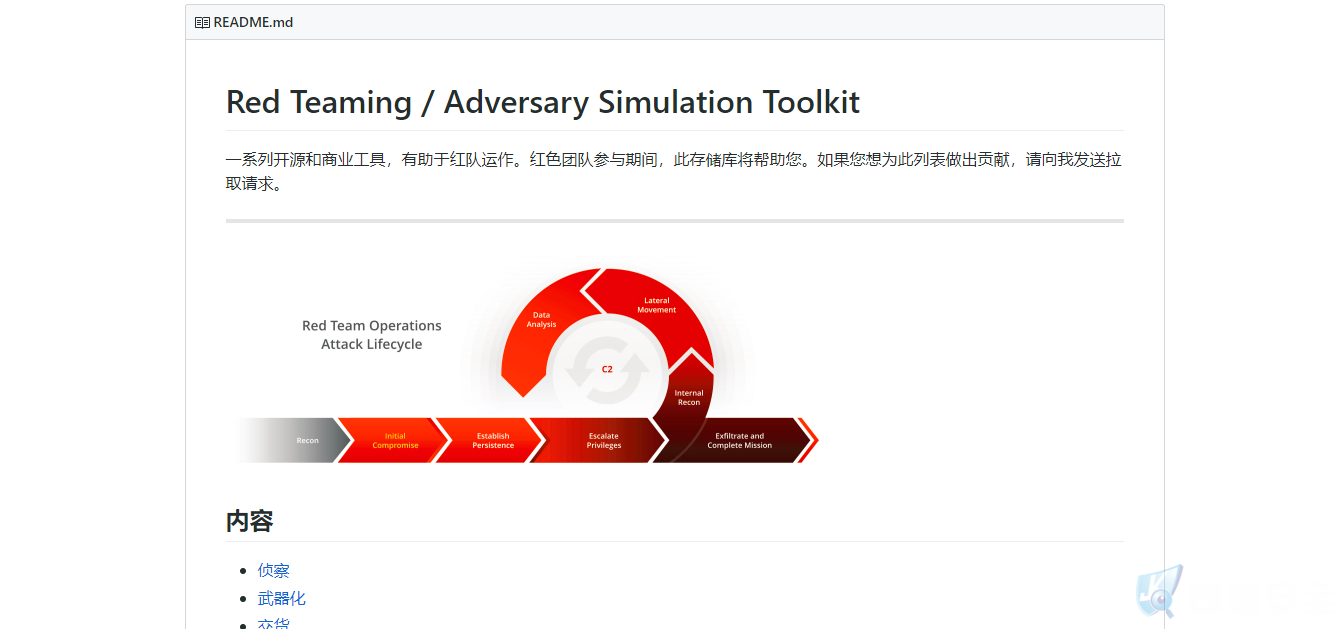
10. DigitalBodyGuard
https://www.digitalbodyguard.com/graydragon.html
11. 深度防御 – 微软的方式(第48部分):傻瓜的特权升级 – 他们没有让这个愚蠢的失误?
http://seclists.org/fulldisclosure/2017/Jul/11
12. JavaScript Web应用程序和服务器易受ReDoS攻击
https://www.bleepingcomputer.com/news/security/javascript-web-apps-and-servers-vulnerable-to-redos-attacks/
13. 从Workstation到Domain Admin:为什么安全管理不安全以及如何解决问题(pdf)
https://i.blackhat.com/us-18/Wed-August-8/us-18-Metcalf-From-Workstation-To-Domain-Admin-Why-Secure-Administration-Isnt-Secure.pdf
14. Linux缓冲区溢出x86第2部分(覆盖和操作RETURN地址)
Linux Buffer Overflows x86 Part -2 ( Overwriting and manipulating the RETURN address)
15. Foreshadow Attacks – 发现3个新的Intel CPU侧通道缺陷
https://thehackernews.com/2018/08/foreshadow-intel-processor-vulnerability.html
转载请注明:即刻安全 » 每日安全动态(8-20)







